Droids
Steps
- Open the droids.jar file in a java decompiler
- Find class files
- Find flagcheckin.class main function file
- Find function detailing flag reconstruction process and relevant files
- Use the Strings in the .class files to reconstruct the flag
- Submit and verify the flag.
Detailed Explanation (Including Screenshots)
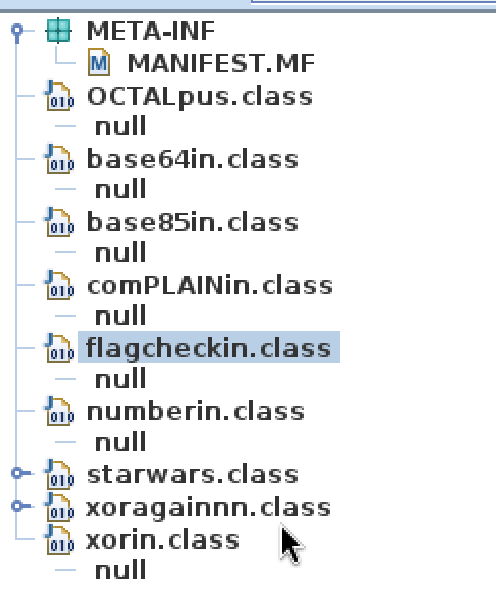
This problem gives a droids.jar file. I attempted to run the file with java -jar, but it was missing its main attribute. I decided to open the droids.jar file in my java decompiler
This showed me all of the class files, I decided to first open the flagcheckin.class file.
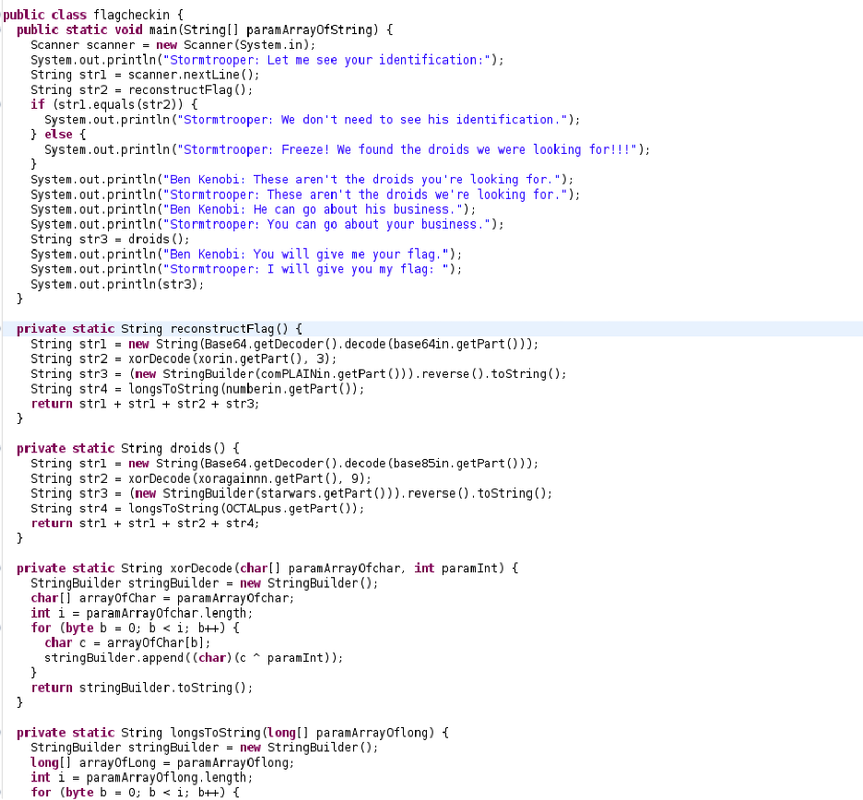
It contained the static void main, so it is the main class in the file.
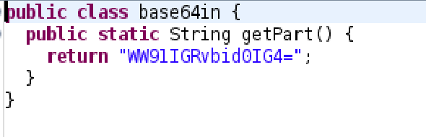
The reconstructFlag() looked like it could be my answer. It shows the base64in file contains a base64 string that is decoded:
It does, I put it into CyberChef: 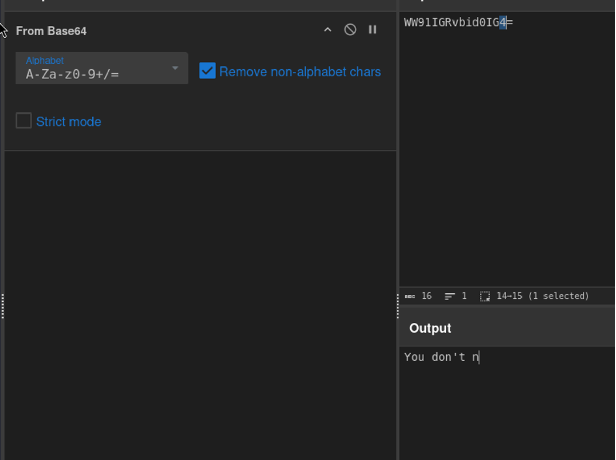 This is plaintext and doesn’t look like what I need. I moved onto the next function
This is plaintext and doesn’t look like what I need. I moved onto the next function droids():
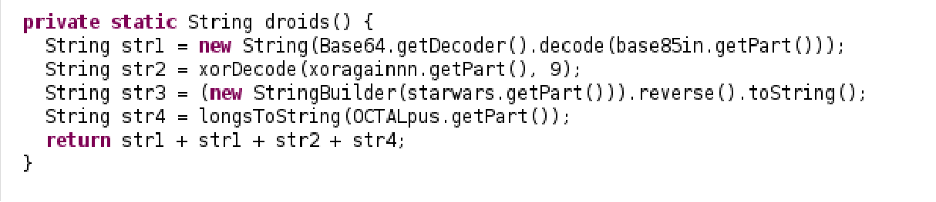 This again contains instructions decoding the strings found in the .class files. It:
This again contains instructions decoding the strings found in the .class files. It:
1
2
3
4
• Decodes the base85 strings in base85in.class
• XORs the string in xoragainnn.class with 9
• Reverses the string starwars.class
• Converts the octal in OCTALpus.class into a string
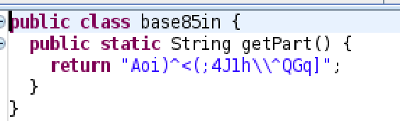
The first is to decode the base85 string in the base85in.class file:
Because “\\” is an escape sequence for printing “\” in java, I need to remove it before I decode the string:
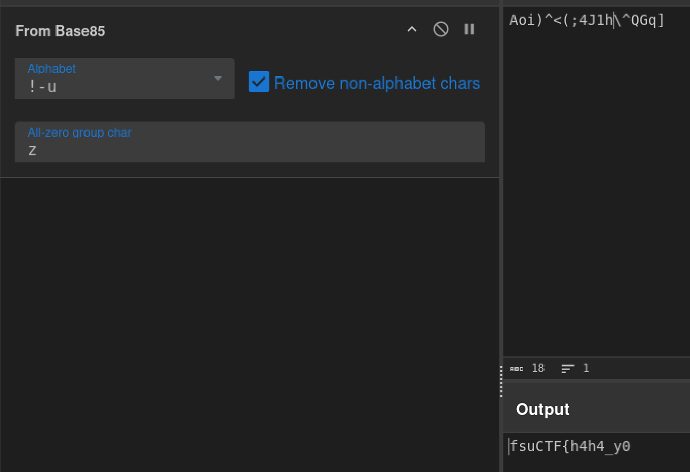 This gives the first part of the flag
This gives the first part of the flag “fsuCTF{h4h4_y0, so it looks like the reconstructFlag() function was a decoy. Next is to get the string xoragainn.getPart() and XOR it with 9
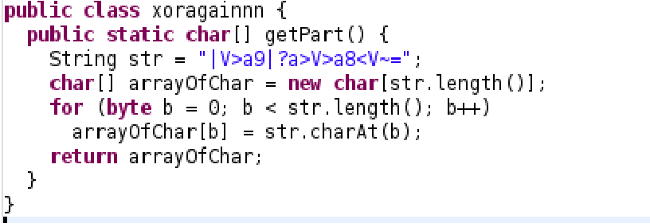
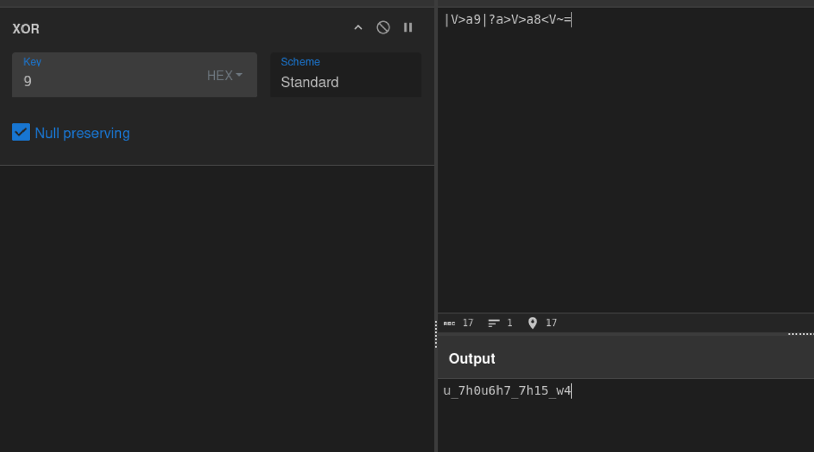 This gives us part 2:
This gives us part 2: u_7h0u6h7_7h15_w4 Next is to reverse the string in starwars.getPart(): 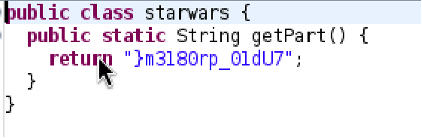
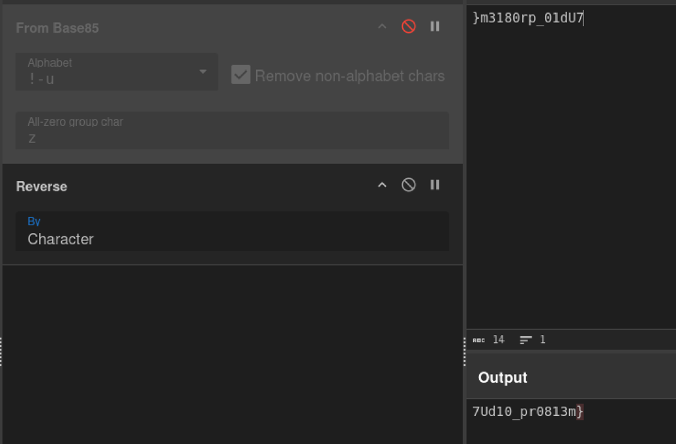 This part of the string is
This part of the string is 7Ud10_pr0813m} This doesn’t seem like the part that follows as it doesn’t match the last and has the closing brace
Next to to decode the octal in OCTALpus.getPart(): 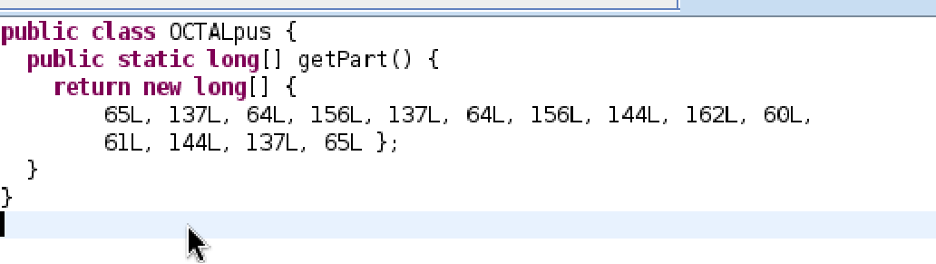
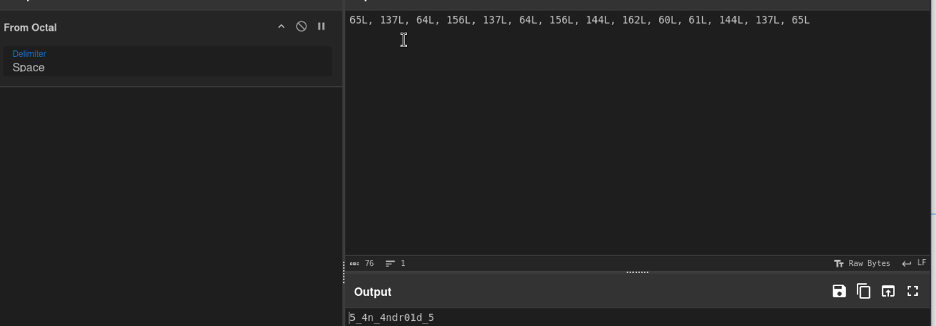
This gives the 3rd and final part: 5_4ndr01d_5
The flag together is: fsuCTF{h4h4_y0u_7h0u6h7_7h15_w45_4n_4ndr01d_57Ud10_pr0813m}
I submitted the flag and verified it.