Four Nations
Steps
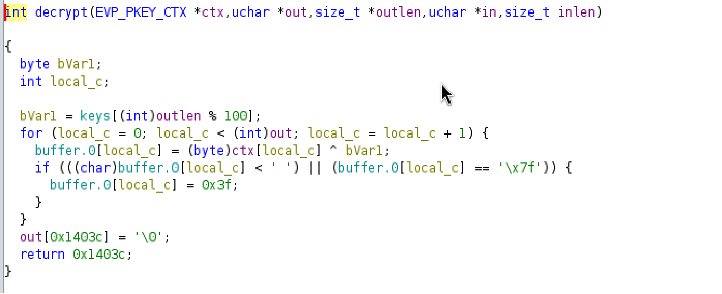
- Reviewed the decompiled binary to understand that it performs four elemental tests by decrypting encrypted scrolls using XOR with a key.
- Identified that each decryption key is chosen by taking the corresponding verification function’s return value modulo 100 and using that index on a fixed keys array.
- Computed the keys for each test
- Earth: 40→key 5;
- Fire: 777→key –70;
- Water: 326→key –81;
- Air: 110→key –98).
- Decrypted each encrypted scroll by XORing every character with its respective key.
- Concatenated the decrypted parts and appended the closing brace to form the final flag
Detailed Explanation (Including Screenshots)
For this problem we are given a binary file. I put the binary file into Ghidra to analyze it:
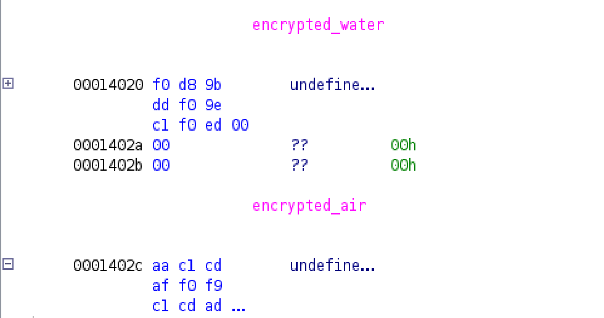
The code shows that the program conducts four elemental tests: Earth, Fire, Water, and Air and that each test involves decrypting an encrypted “scroll.”
I noted that every decryption routine takes an encrypted string and XORs each of its bytes with a key obtained from a fixed keys array. 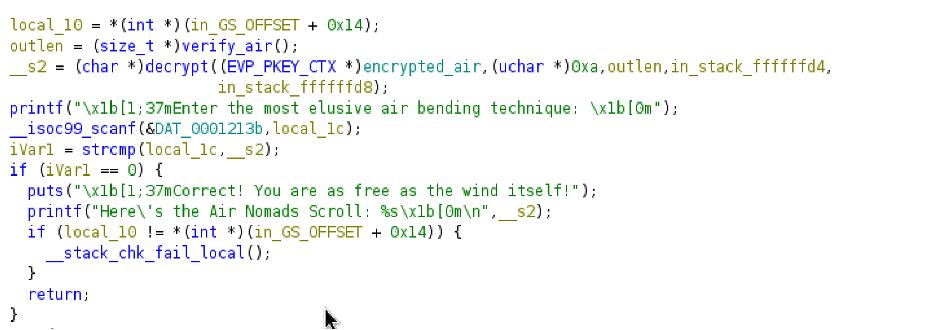
Next, I examined how the decryption key is chosen. The program calls a verification function (such as verify_earth) for each test, and then computes the key by taking the returned value modulo 100 and using that as an index into the keys array. This means the key is calculated using the formula:
key = keys[verify_function_return % 100]
Using the information provided by the decompiled code, I then computed the decryption key for each test.
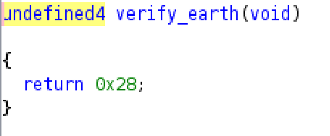
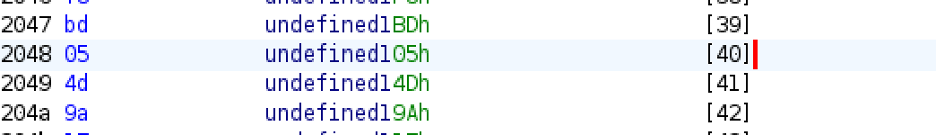
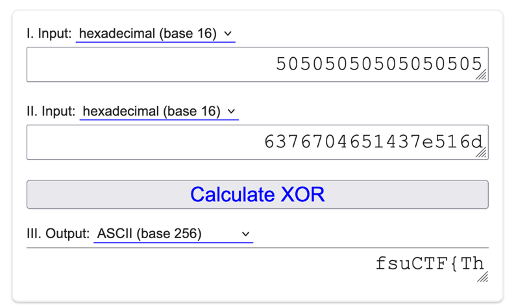
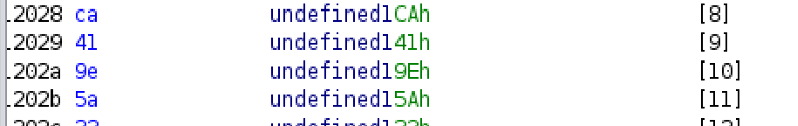
For the Earth test, verify_earth returns 40 (0x28), so the key is keys[40] which equals 05 from our keys array
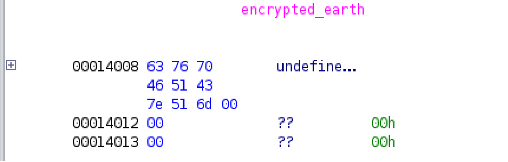
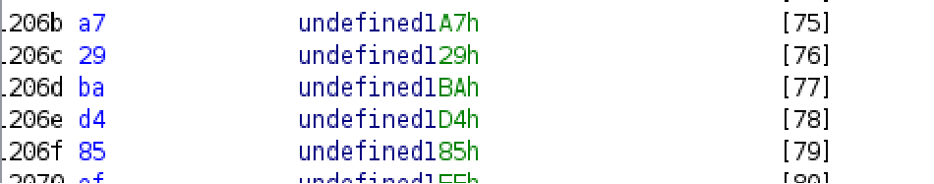
I got the encrypted “scroll” from the data section for earth and XORed it with 05
This gives the first part of the flag fsuCTF{Th
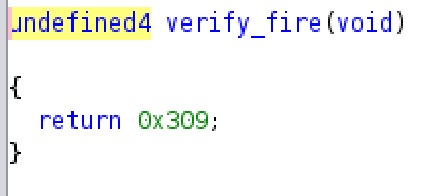
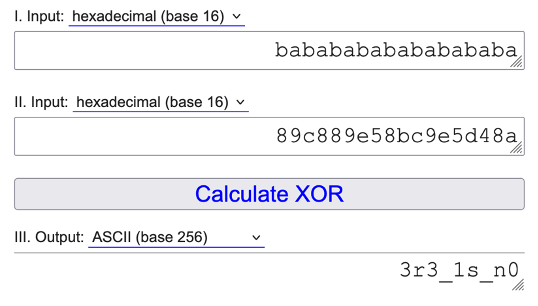
For the Fire test, verify_fire returns 777 (0x309), and 777 mod 100 gives 77, so the key is keys[77] which equals ba in our keys array
This gives the next part of the flag: 3r3_1s_n0
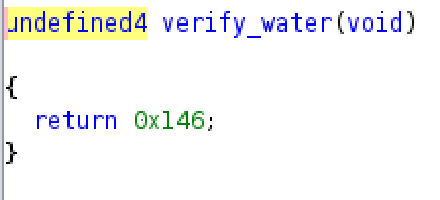 I then XORed it with its encrypted string:
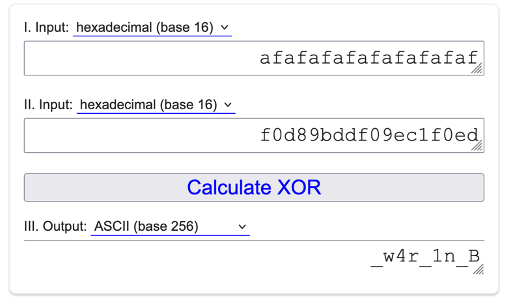
I then XORed it with its encrypted string:
This gives us the next part: _w4r_1n_B
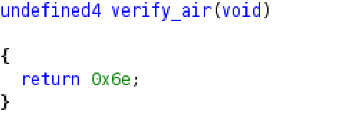
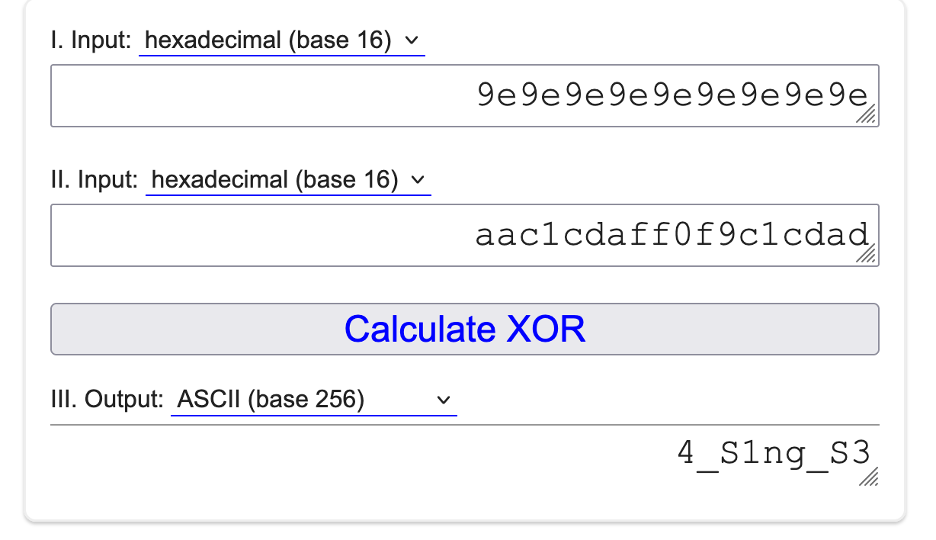
And for the Air test, verify_air returns 110 (0x63) (resulting in keys[10] = 9e).
I XORed it with its string and got:
With this we can now compile the entire flag: fsuCTF{Th3r3_1s_n0_w4r_1n_B4_S1ng_S3} I submitted and verified the flag